A complex and adaptive problem
One challenge many large organizations encounter when developing cyber security strategies is how to adequately protect digital assets from adversaries that are smaller and more agile.
- Agility
- Rapid decision cycles
- Situational awareness
- Intelligence
- Intelligence-led strategies
The methods employed by every organization will vary, but the issues canvassed here represent a strong starting point for helping your organization think about strategies to strengthen the security of your digital assets.
Adopting a threat centric approach to cyber security
Agility. Flexibility. Transparency.
In the business world, each of these is a worthy attribute. Corporate leaders understand that each of these attributes helps deliver better business outcomes. However, in recent years the business world has profoundly changed as a result of the emergence of cyber threats and the disruption this has caused.
Achieving a conducive business environment whilst simultaneously mitigating your cyber risk is possible if business leaders think beyond technology risk management. By adopting a threat centric approach to cyber risk management, which focuses on the mindset and capabilities of adversaries, business leaders will be better prepared to embrace disruption.
1. Agility
Business leaders often focus cyber security efforts on technology to manage risk.
Whilst good risk management practices should always focus attention on effective cyber security, the threat landscape is constantly evolving.
Business leaders need to think beyond technical risk management. It begins by recognising that cyber threats are both complex and adaptive. By adopting an agile and threat-centric approach, which focuses on the mindset and capabilities of adversaries, business leaders will be better placed to secure their systems and critical data.
There are four key reasons why cyber security is a complex problem:
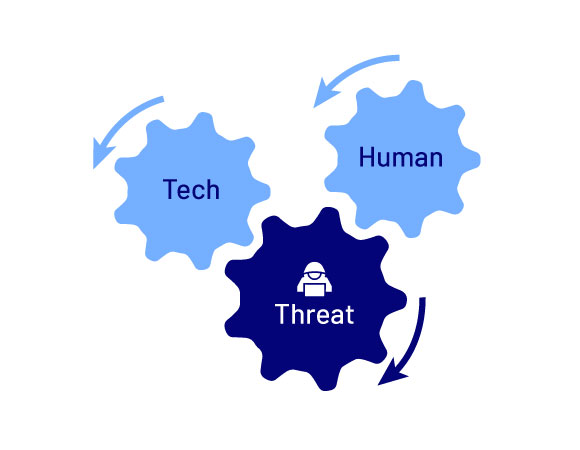
a. Three overlapping elements: technology, threats and human behaviour
Often, businesses understand one or two of these elements, but rarely all three.
Your IT team may understand technology. Your risk assessors may understand how to calculate threats. Your staff trainers may understand the human element.
However, it is essential as a business leader that you find ways to incorporate all three elements when thinking about cyber security. A holistic picture, in which each of these elements overlaps and interacts with the other two in multiple ways, is essential.
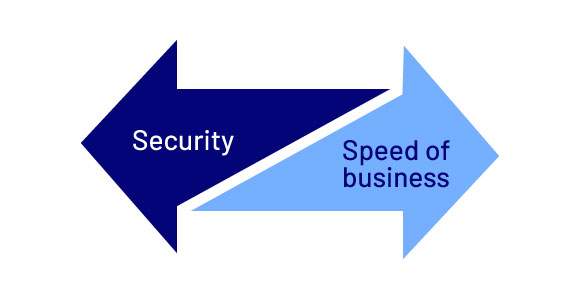
b. Conflicting priorities: security vs speed of business operations
To be competitive, businesses must act with speed and agility. Even in the event of a compromise, such as a cyber incident, businesses cannot afford to simply halt their operations. To survive, the business must continue operating.
Therefore, as a business leader, you have an obligation to prioritize business continuity, even in the face of a security breach. With effective risk analysis and business continuity planning, it is possible to strike the right balance between these competing imperatives.
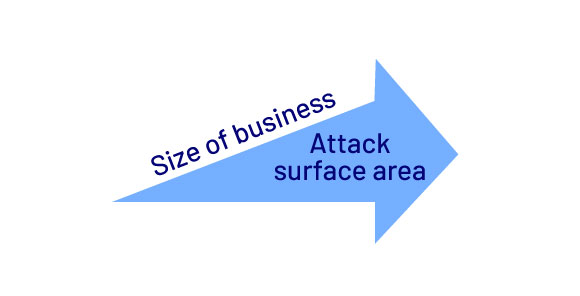
c. Ever expanding attack surfaces
Paradoxically, the more technology your business implements to secure your systems, the larger your exposure grows. This is because technology can expand your attack surface area, providing adversaries more opportunities to breach your systems.
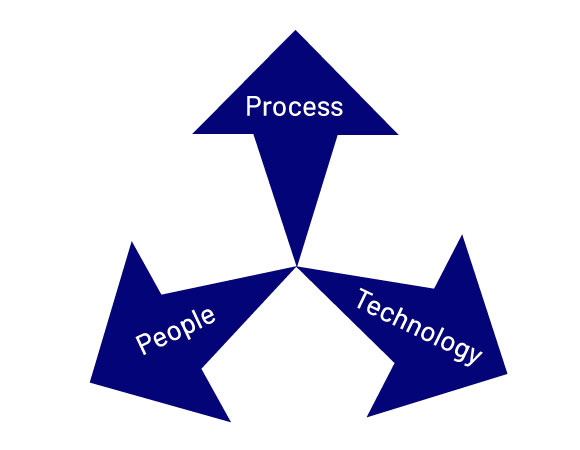
d. A need to balance people, processes and technology
To have a holistic cyber security strategy, it is imperative to balance people, processes and technology.
All too often, business leaders over invest in technology as a result of mistakenly thinking cyber security is all about IT. Whilst buying the latest products can make business leaders feel they are taking cyber security seriously, it won’t strengthen their robustness without the right processes in place to integrate the important learnings from that technology.
Likewise, investing in people is lagging. Adversaries increasingly target individual employees, deceiving them into granting access to the environment.
2. Rapid decision cycles
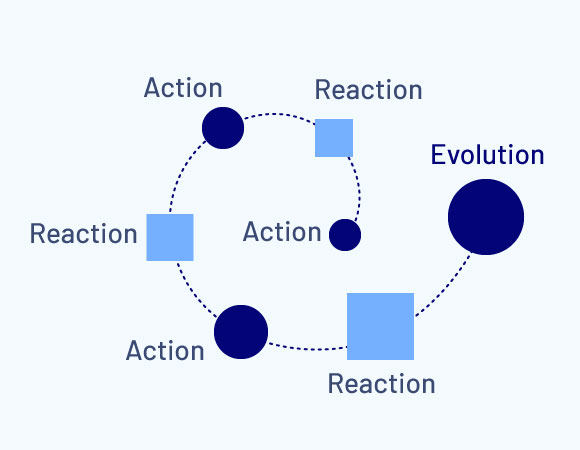
Not only is cyber security a complex problem, it is also an adaptive problem that undergoes change over time. This is due to the fact that organizations react to every action an adversary takes. This in turn triggers the adversary to have a subsequent reaction.
As this sequence continues over time, it eventually leads to an evolution in the threat problem.
This becomes clear when taking a longer-term perspective. Cyber threats in the 1990s were quite different to today. It is clear they have gone through a series of evolutions over time.
The challenge is identifying what drives the speed of that adaptive evolution. Speed is driven by decision cycles. The larger the organization, the longer the decision cycle.
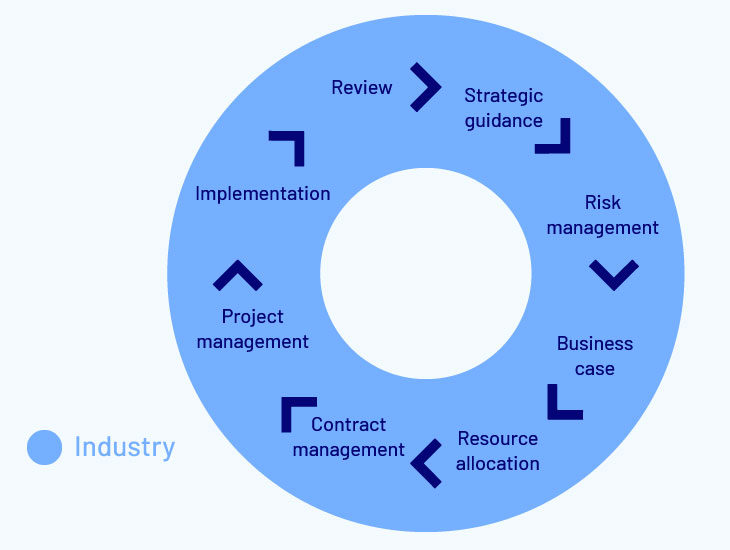
For example, if an organization was considering a new security strategy, or implementing new security controls, there would likely be a number of lengthy stages. Firstly, the board would need to set the risk appetite and provide strategic guidance. Executives would then begin looking at implementation options. Risk managers may be brought in to analyse the options before a business case could be developed. This would generally trigger a decision to make some strategic commitment or investment, which in turn requires resource allocation. This may require contract management and project management. Only at this stage would the organization get around to implementation, which should then be followed after a period of time by reviews to determine the utility and efficacy of the initiative.
As you can see, this is a very long cycle that may take months or years to implement, refine and optimize.
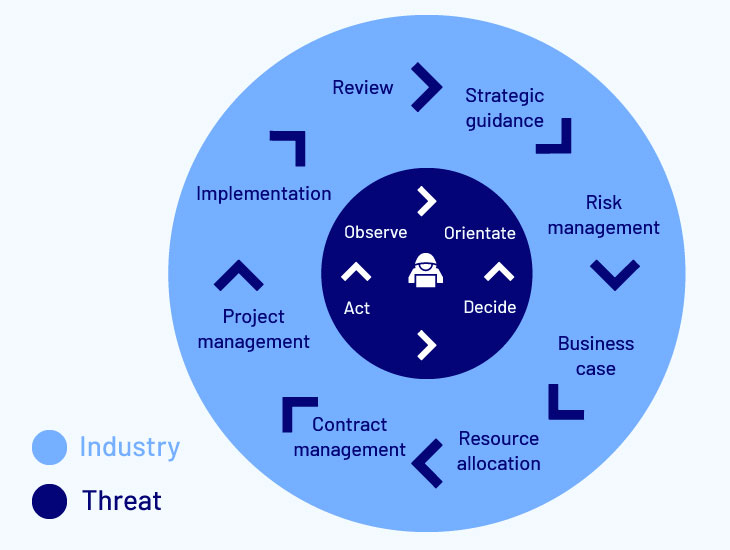
By contrast, adaptive adversaries can operate according to much shorter cycles.
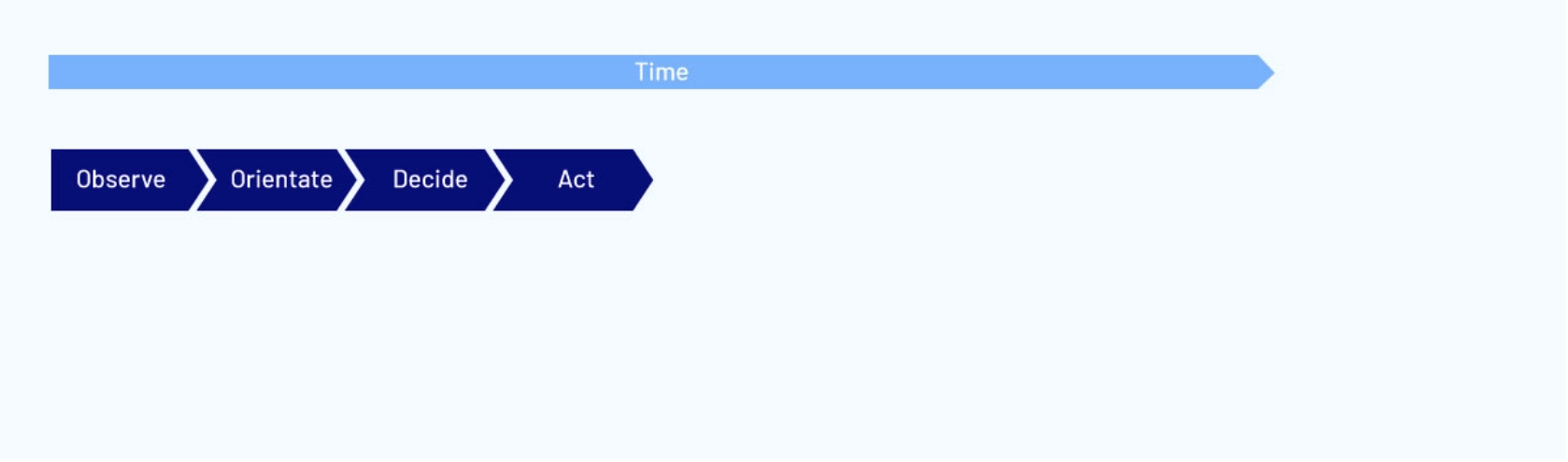
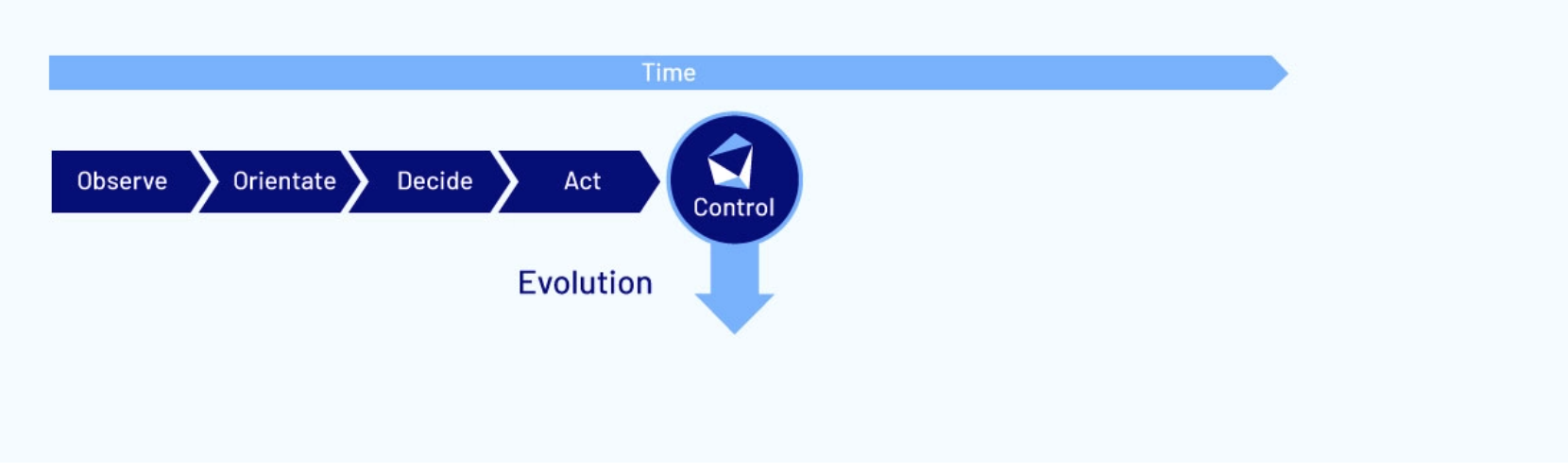
This short cycle is often characterised as the OODA loop:
- Observe
- Orientate
- Decide
- Act
With far fewer stages than a large organization’s decision-making cycle, the OODA loop allows adversaries to move much faster.
Businesses traditionally operate according to 12-month cycles. By contrast, cyber adversaries tend to be far more responsive to changing circumstances thanks to their ability to make decisions on a daily or weekly basis.
Despite being larger and having significantly more resources, it is all but impossible to effectively battle adversaries with short decision-making cycles that fit within the large organization’s long decision-making cycle.
The challenge for any large organization is to find ways to react or evolve much more quickly. When a large organization evolves slowly, it is likely to be vulnerable to a range of compromise events or breaches by adaptable adversaries.
Larger organizations must find ways to evolve at the same speed, or preferably slightly faster, than their attackers. Rather than maintaining rigid 12-month plans, daily or weekly decision-making cycles that facilitate rapid responses to constantly changing threat landscapes is preferable.
Having said that, it is also important that large organizations do not evolve too quickly, which indicates an over-investment that isn’t sustainable in the long term.
3. Situational awareness
It is currently not feasible to defeat all cyber adversaries or mitigate all cyber threats. At best cyber adversaries and threats can be disrupted.
The key to fighting an adversary is to look carefully at what capabilities or inputs they need to successfully carry out an attack. As a business leader, you need to identify which of those capabilities and inputs you can disrupt. In this way it is possible to establish an edge over the enemy.
Cyber threat actors generally require the following in order to carry out an attack:
- TRAINING: Adversaries are able to self-learn how to carry out an attack.
- TACTICS: Successful attack strategies are freely shared among adversaries.
- TOOLS: The tools for carrying out attacks are generally free and easily accessible.
- ACCESS: Using the internet, a threat actor can access targets anywhere in the world, at any given time.
- TIME: Threat actors, particularly highly skilled ones, have many targets to choose from. As with any occupation, time is money. Therefore, adversaries need to be judicious and select targets that don’t require the investment of too much time.
Of all these essential capabilities and inputs, large organizations only have influence over the last one: Time. By creating a “time penalty,” it is possible to disrupt an attacker to the point that they opt to switch targets.

Forcing attackers to pay a “time penalty” is not just a function of actual security controls. It also comes from perceived security controls. In other words, looking secure matters as much as being secure. When an attacker conducts reconnaissance on potential targets, those appearing secure may be bypassed, without the attacker bothering to test the strength of any actual security controls.
4. Intelligence
Once you accept that the problem of cyber adversaries never really goes away and the best any organization can hope to achieve is to disrupt their attacks, it becomes clear that you need effective and efficient cyber controls. The fact that cyber threats are constantly evolving, and you will forever need to defend against them, means you cannot afford to over invest.
Rather, you need to opt for the right investments at the right places and at the right time.
This requires a clear analysis of the threats you face, bearing in mind that the most dangerous threats may not be the most likely threats.
For example, critical infrastructure may find that the most dangerous threat is also the most likely, because such assets tend to be targeted by adversarial nation-states. However, for other organizations, the most likely threat is unlikely to be the most dangerous. Therefore, investing in controls to prevent the most dangerous threats may not be the best strategy.
5. Intelligence led strategies
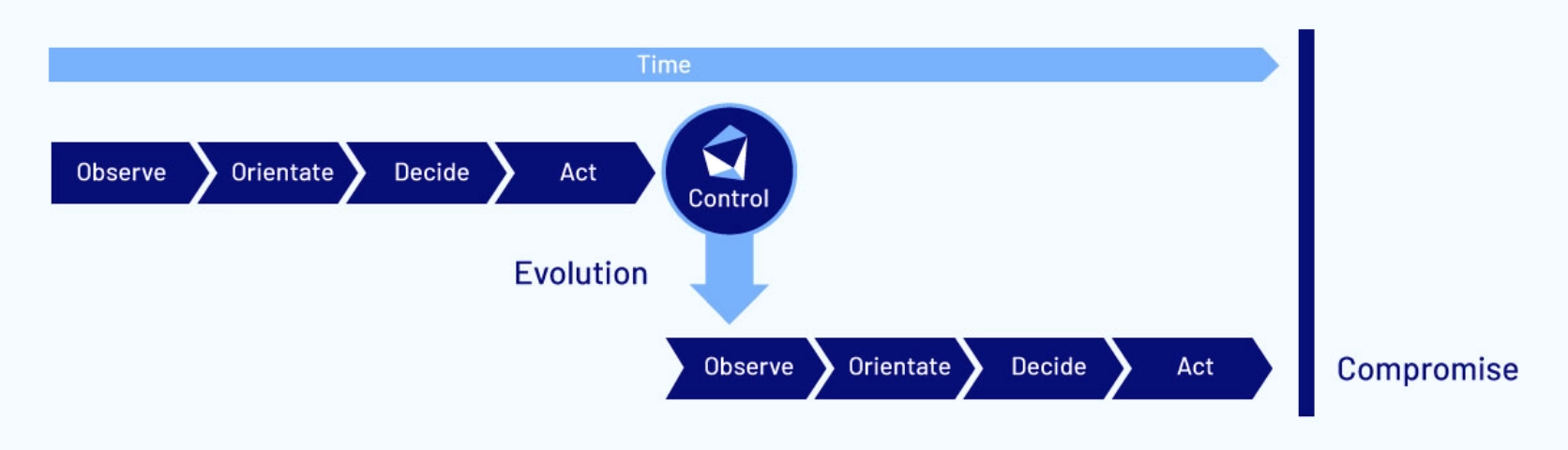
As mentioned above, over time threat actors operate according to the “OODA” cycle:
By the time the adversary is prepared to act against you, if you have no security controls, an attack is likely to succeed.
However, if you have a security control that prevents them attacking you successfully, they will likely evolve and target you in a different way:
Many organizations fail to take into consider this evolution. They tend to implement controls and assume they are safe. This is a mistake. With threats constantly evolving, organizations also need to continuously review and adapt their security controls.
Threats may evolve through the adoption of new tactics, or you may implement new technologies that expand your attack surface. Either way, security controls must be continuously updated in order to continuously disrupt attackers.
That’s why we always advocate an “adaptive” approach to cyber security. Information security standards, such as ISO 27001, adopt a risk centric approach and require constant validation of security controls. These validation exercises create triggers that prompt the organization to enhance and continuously improve their security controls.
Through uplifting your controls in this way, it becomes possible to disrupt threat actors. However, an attacker will likely evolve and attempt new modus operandi. However, if the organization has been able to implement decision-making cycles that are fast enough, additional controls can be put in place to disrupt the newer attack vector.
As an organization builds up its security controls, most of the likely threats will be blocked. Over time, even the less likely, but more dangerous threats, will also be blocked. The process of
constant validation and enhancement ultimately leads to a significant increase in the time an adversary needs to invest into a breach.
The goal is to disrupt attackers enough that they are prompted to move on to a different target.

When designing a security strategy, you should tailor it to meet your specific circumstances and enhance your strengths, whilst mitigating your weaknesses. It should allow you to be adaptive and have a decision-making cycle that ensures you can evolve at the same rate, or slightly faster, than most of the adversaries you’re likely to face.
That’s why any effective cyber security strategy needs to be shaped by intelligence. It’s essential to have a thorough understanding of the specific threat actors, so the right controls can be implemented in order to disrupt them.
There is not a one-size-fits-all approach to cyber strategies.
The nexus between business leaders and cyber threats

We began this discussion looking at the relationship between business leaders and cyber threats. At this point, it is essential to consider how threats and leaders interact with each other.
Perhaps the most important way business leaders can enhance their organization’s security is by driving and shaping a culture of cyber awareness. For many organizations in the commercial world, security is a relatively new problem. As stated at the beginning, the private sector tends to prioritize agility, flexibility and transparency as these drive optimal business outcomes.
So, introducing a security awareness culture can be a challenge.
Whilst cyber threats target organizations with underdeveloped security cultures, intelligence can be used to develop appropriate strategies that include security awareness at the core.
In summary, the five key elements in addressing complex adaptive threats include:
- Agility: This is superior to power or resources as it allows you to adapt quickly.
- Rapid decision cycles: Agility can be achieved when you have the capacity to make decisions slightly faster than your adversaries.
- Situational awareness: This helps trigger rapid decision-making processes because you understand what’s going on at any given point in time.
- Intelligence: This enhances your situational awareness as it is about understanding your own context, your own business, your own attack surface area, as well as understanding what potential threats are doing, or are likely to do.
- Intelligence-led strategies: These give you an edge in a complex adaptive adversarial contest.
Through the implementation of a threat centric mindset, your organization can gain the upper-hand in fighting a range of cyber adversaries.