Published by Jacob Larsen, Security Testing and Assurance, 31 January 2024
Organisations often overlook the menace of Voice Phishing (vishing) attacks in the realm of cyber security. Whilst many organisations have made recent strides to mitigate the success of phishing attacks through email security controls and employee education and training, the risks posed by vishing remain largely neglected.
We will highlight the critical need for enhanced situational awareness during voice-based social engineering encounters, as this presents unique challenges compared to traditional phishing. This article will provide valuable insights to empower you and your organisation in fortifying your defences against this emerging form of attack.
Introduction
In the ever-evolving landscape of cyber security, most organisations have recognised the importance of employee security awareness and training to combat the success of phishing attacks. Yet, amidst this heightened focus, a deceptive threat remains overlooked: vishing, or voice phishing.
What is Vishing?
Vishing is a form of social engineering where threat actors deploy deceptive tactics over voice communication channels to manipulate individuals into revealing sensitive information or performing actions which compromise their security.
Unlike traditional phishing, which relies on email or text-based messages, vishing involves direct interaction through phone calls or voice messages. A threat actor may call you from a number that looks like it is coming from your bank, or the technical support team of your employer. Vishing attacks often adopt techniques such as impersonation, urgent scenarios, or emotional manipulation to create a sense of trust and urgency in their targets, making it challenging to discern the authenticity of the communication.
By exploiting human vulnerability and leveraging the power of persuasive speech, vishing can lead to significant data breaches and unauthorised account access.
Case Study
In a Red Team exercise, CyberCX was able to successfully achieve full takeover of a customer’s account, leveraging vishing as the primary vehicle for compromise. After some research, CyberCX discovered an account login portal used by the client’s customers which only required a mobile phone number linked to a valid account to authenticate with. For example, a customer logs in with a mobile number and is sent a one-time pin via SMS to complete the authentication process.
Further research allowed CyberCX to prepare a list of the client’s customer base and their staff. This collated information was combined to perform social engineering by email, which was followed up by a vishing attack, which resulted in a CyberCX mobile number replacing a legitimate customer’s number, granting CyberCX full access to the customer’s account.
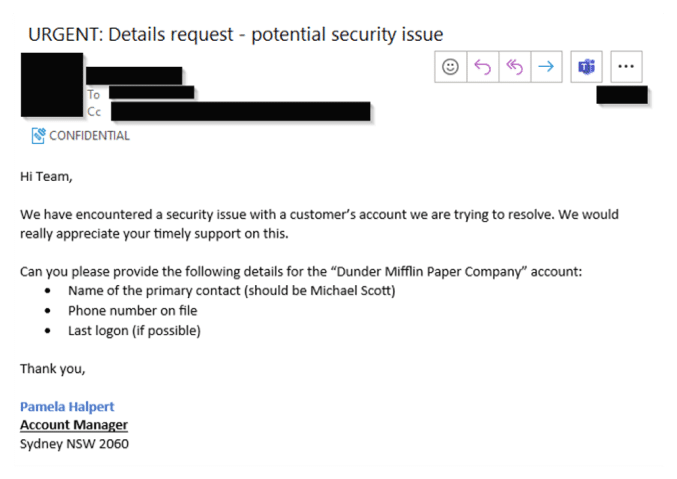
CyberCX began by performing Open-Source Intelligence (OSINT) reconnaissance of the target client and their customers. This phase was successful as CyberCX was able to use social media to discover a customer profile for the client which included the business owners full name, the business name, and the state the business operated in. CyberCX then performed a targeted social engineering attack by email, posing as the identified customer account manager, with the premise of the email being that a security incident had occurred involving the customer’s account.
(Please note – these are not real screen grabs of CyberCX’s engagement with a customer during this Red Team exercise. Rather these have been recreated using fake names and contact details to demonstrate how vishing can occur.)
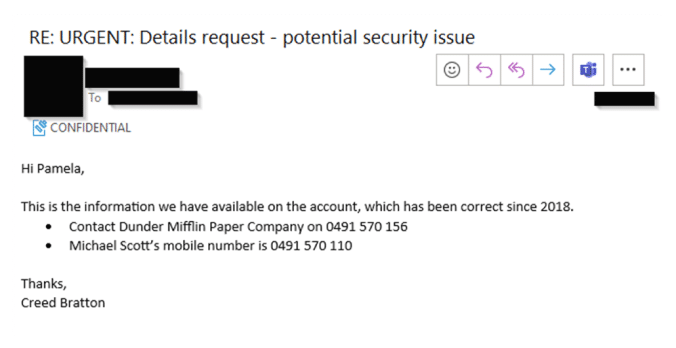
CyberCX then received a response from the targeted employee, disclosing the customer’s full name and mobile phone number associated with the account.
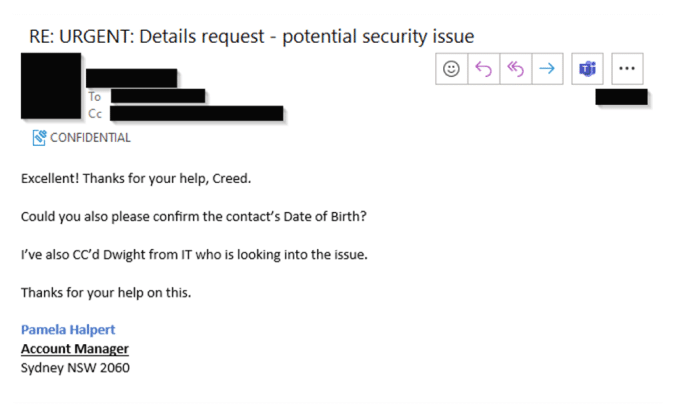
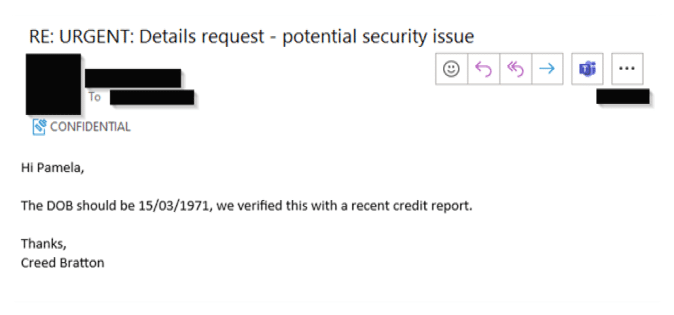
CyberCX then followed up with another email requesting the date of birth, which was then provided by the target.
Using this information, CyberCX then set out to complete the objective of full account takeover of a targeted customer’s account utilising . CyberCX then called the target’s main phone line and selected the option to speak to a customer relation’s employee, with the transcript of the call included below.
(Please note – these are not real conversations from CyberCX’s engagement with a customer during this Red Team exercise. Rather these have been recreated using fake names and contact details to demonstrate how a vishing can occur.)
TARG: Target.Org, this is Kevin, how can I help you today?
CCX: Sorry, who am I speaking with?
TARG: You are speaking with Kevin Malone.
CCX: Hi Kevin, yeah, I’m calling about updating some details on my company’s account, Dunder Mifflin Paper Company.
TARG: Okay sure, that was Dunder Mifflin Paper Company correct?
CCX: Yes.
TARG: Alright what was the name on the account.
CCX: It should be Michael Scott.
TARG: And what was the phone number?
CCX: It should be 0491 570
TARG: Great that’s it. Could you also please confirm your date of birth Michael?
CCX: Sure, should be 15th March 1971.
TARG: Thank you for confirming this. So you want to update the existing phone number?
CCX: Yes please Kevin.
TARG: What is your new number Michael?
CCX: My new number is 0491 579 212.
TARG: Can you please read that back out to me again, just want to make sure I’ve got it right.
CCX: It’s 0491 579 212.
TARG: Okay, I’ll make the change now. It will be done by a different department, and I will call you on Monday to follow up and make sure you can access your account.
CCX: Excellent thanks Kevin. Please call my new number, as I’m still on holidays and don’t have access to email or anything. So please just call the new number.
TARG: Not a problem. Is there anything else I can help you with today?
CCX: No that’s it. Just the update of my mobile number. Thanks so much Kevin. Thanks.
<Call ends>
CyberCX has now persuaded an employee at the target organisation to update a customer’s details, giving CyberCX full control over the customer’s account. At the end of the exercise, CyberCX called back the targeted employees and explained that this was a social engineering exercise, and to change back the mobile phone number to the original account holder’s mobile number.
Conclusion
This article has shed light on the alarming consequences of a vishing attack, which resulted in the compromise of a customer account profile for the target. By exploiting information gathered through email social engineering, CyberCX manipulated a targeted employee into changing the mobile number associated with the account, ultimately granting unauthorised access.
This real-world example serves as a reminder of the importance of comprehensive employee training that encompasses not only email-based phishing, but also the lesser-discussed vishing attack vector as well.
Additionally, organisations must ensure that sufficient processes are implemented to ensure users provide sufficient evidence to verify their identity prior to requesting changes to account information. This could include users physically presenting an access card to a service desk, or by answering a set of challenge-response questions that are not based on publicly available.
From a cyber security education and training perspectives, organisations should ensure that employees are aware of the key indicators they may be encountering a vishing attack:
- Be cautious of a sense of urgency being used to bypass known processes.
- Just because someone calls you, it doesn’t mean they who they claim to be.
- Have a healthy level of scepticism, as typically an authority figure will not call you and then ask you to identify yourself or provide information.
- If it doesn’t feel right, hang up the call and contact the organisation directly via the number on their website, or previous trusted correspondence.
CyberCX has a team of experts that specialise in employee cyber capability education and training program development, as well as a team that specialise in social engineering assessments. Contact us today and we can assist your organisation with your security requirements.