Cyber Security Risk Assessment
Cyber Threat and Risk Assessment Services
Secure your organization with a Cyber Threat and Risk Assessment. Gain insight into your organization’s current cyber risk profile, protect what is important and make informed decisions to strengthen your security posture.

The cyber threat landscape facing the US organizations is more complex than ever before. Adversaries continue to grow in number and capability, alongside a rapidly shifting geopolitical landscape and evolving technologies.
The complexity of the threat landscape is intensified by enhanced consumer expectations in relation to cyber security and data privacy, in addition to emerging and competing regulations, legislation, standards, and an ever-increasing reliance on technology systems.


Benefits of a Cyber Threat and Risk Assessment
A Cyber Risk Assessment gives you an unbiased perspective on weaknesses and potential cyber threats to your organization.

Tailored to the organizational requirements
Threat and risk assessments can be tailored depending on your requirements, from a single system or process to an entire organization. The scope can be completely customized depending on the subject of the risk assessment.

Improve your cyber security posture
Gain an understanding of your organization’s current level of risk and work towards improvements informed via a prioritized roadmap of recommendations. A Cyber Threat and Risk Assessment will provide a holistic picture of the strengths, weaknesses and recommendations of the assessed organization, process or system.

Understand and manage risk
Understanding risk can allow organizations to manage potential harm from a financial, reputational and operational perspective. The subject of risk can be complex and challenging to manage. A Threat and Risk Assessment will provide clear and targeted guidance for the ongoing management of your organization’s various risks.

Protect your people and systems
Understanding risk allows for the proper protection of what is important to your organization. Safeguard sensitive data and maintain trust in your organization both internally and externally.


An Intelligence-Led Approach To Cyber Threat and Risk Assessments
Cyber intelligence enables organizations to understand the threat and to implement appropriate and effective risk measures to respond to that threat. The US and global organizations are increasingly taking an intelligence-led approach to managing cyber risk.
Cyber threat actors are adaptive, the geopolitical landscape changes quickly and technology is always evolving. At the same time, cyber budgets are constrained, despite regulatory and market pressure to always do more.
We help you to understand the threats that are relevant your external environment, so you can make better decisions about managing risk in your internal environment. Intelligence-led threat and risk assessments help to better prioritize and allocate resources, and triage threats for action.



What is a Cyber Threat and Risk Assessment?
A Cyber Threat and Risk assessment evaluates the level of risk associated with the target organizational assets. Assessments can be targeted to a specific system or process, or more broadly across the wider organization. CyberCX evaluate and provide findings to organizations on their current risk profile, identify potential threat and provide recommendations for improvement and a lowered risk rating within the business tolerance.
Who should consider an assessment?
All organizations require an understanding of their cyber risk environment but it may be due to different business drivers. An independent threat and risk assessment is suitable for organizations of all sizes implementing new processes or systems or making major organizational changes. Threat and risk assessments can be tailored depending on your requirements, from a single system or process to an entire organization. An annual risk review will allow you to track your progress over time and validate changes to internal operations.
Why is an assessment important?
Whilst regular internal risk evaluation and treatment is necessary, an outsourced and independent assessment can provide an unbiased perspective on potential threats and weaknesses. Recommendations can be tailored to a prioritized roadmap within organizational restraints, such as resourcing and technology.


Cyber Threat and Risk Assessment methodology
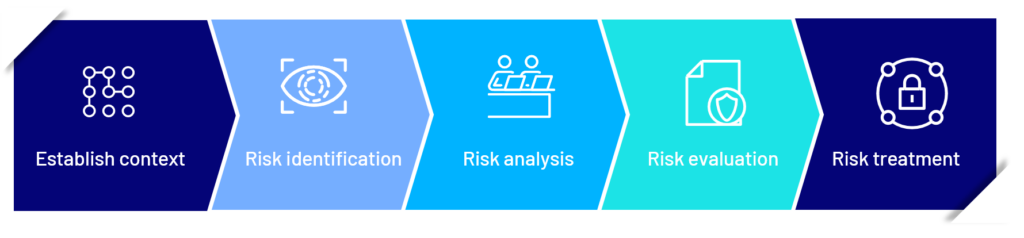
Firstly, our consultants gain an understanding of your organization’s assessment context. Consultants will then step through a process to identify relevant assets and current controls. From there, potential threat and vulnerabilities will be identified. This will allow for the risks to be analyzed and evaluated, and recommendations to be determined and prioritized.
- Establish context
- Risk identification
- Risk analysis
- Risk evaluation
- Risk treatment

Ready to get started?
Find out how CyberCX can help your organization’s cyber security posture by conducting a risk assessment.


Why partner with CyberCX for Cyber Threat and Risk Assessments?
CyberCX is the trusted provider of cyber security and cloud services. With a workforce of over 1,400 professionals, we are a trusted partner to private and public sector organizations helping our customers confidently manage cyber risk, respond to incidents and build resilience in an increasingly complex and challenging threat environment.
Experience and expertise
Diverse team of cyber risk professionals experienced in assessments across various industries and systems.
Flexible approach
Our flexible approach ensures the entire process is tailored to suit your needs. We work with your internal teams to understand and develop a risk profile and recommendations based on your organizational objectives.


Ready to get started?
Find out how CyberCX can help your organization’s cyber security posture by conducting a Cyber Threat and Risk Assessment.
Cyber Threat and Risk Assessment FAQs
Have a question about risk assessments not covered here?
Contact our team and we’ll be happy to help.
Whilst regular internal risk evaluation and treatment is necessary, an outsourced and independent assessment can provide an unbiased perspective on potential threats and weaknesses.
Firstly, gain an understanding of the organization’s assessment context. Consultants will step through a process to identify relevant assets and current controls. From there, potential threat and vulnerabilities will be identified. This will allow for the risks to be analyzed and evaluated, and recommendations to be determined and prioritized.
A typical Cyber Threat and Risk Assessment can take between 3-4 weeks to complete.
Understanding risk allows for the planning and preparation of proper controls that are important to your organization, safeguard sensitive data and maintain trust both with your internal workforce and external customers. Additionally, it will assist your organization in prioritizing your remediation actions based on the risks most pertinent to your environment.
- Establish Context
- Risk Identification
- Risk Analysis
- Risk Evaluation
- Risk Treatment
- A cyber risk spreadsheet and detailed report including identified threat events, relevant assets, threat actors, current control, identified weaknesses, and recommendations.
- Assessed risk levels for Current, Achievable and Residual risk.

Ready to get started?
Find out how CyberCX can help your organization’s cyber security posture by conducting a Cyber Threat and Risk Assessment.
