Cyber Security Awareness Month: 11 key security practices to improve your organization’s cyber security
11 key security practices to improve your organization’s cyber security
Cyber Security Awareness Month
Now in its 18th year, Cyber Security Awareness Month continues to raise awareness about the importance of cybersecurity across the world. The theme for Cyber Security Awareness Month 2021 is “Do Your Part. #BeCyberSmart.”
The theme empowers individuals and organizations to own their role in protecting their part of cyberspace. If everyone does their part – implementing stronger security practices, raising community awareness, educating vulnerable audiences or training employees – our interconnected world will be safer and more resilient for everyone.
Be Cyber Smart
The first week of Cyber Security Awareness Month is about implementing the best security practices and general cyber hygiene to keep your information safe. Cyber crime is on the rise and hackers will actively exploit any vulnerabilities they find. So, just as you wouldn’t leave your business premises unlocked at night with the safe door open, it’s important you don’t leave your data and systems unprotected.
Using multi-factor authentication, backing up your data, and updating your software are all examples of how you can Do Your Part #BeCyberSmart!
To support this weeks’ theme we have provided some practical key steps you can take to improve your organization’s cyber security and become a more resilient business.
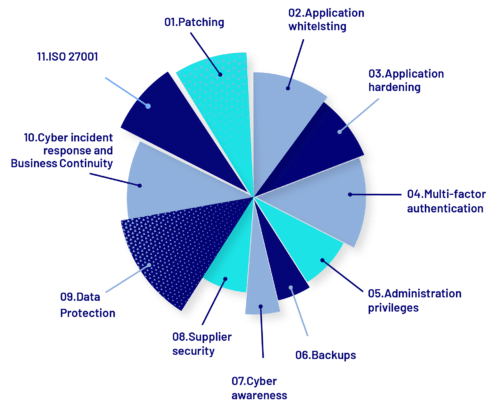
1. Patching
The number of ransomware attacks on businesses continues to grow. By not regularly patching your organization’s networks you are leaving security holes which could enable hackers to plant malware in your systems. This could then enable them to steal data, gain control over your computer and systems and encrypt files.
To minimise the risks to your organization, it’s important that you keep up-to-date with which security patches are available and regularly install updates to patch all of your servers, devices and software as soon as possible.
2. Application Whitelisting
Application whitelisting is the process of allowing only pre-approved applications to run on your organization’s systems. This helps prevent unauthorised, potentially unsafe, software being installed and can block malware from harming your systems.
To get started on whitelisting applications within your organization first you need to create a ‘Whitelist Application Policy’ and complete an audit of applications that different departments/employees use. Once you have gathered this information your IT department can set about whitelisting applications on user platforms as per the audit.
3. Application Hardening
Application hardening is the process of taking an application and adequately hardening it against the risk of attacks. Application hardening is a best practice for companies to protect their application’s intellectual property and prevent misuse, defacement and potential exploitation.
Application hardening can include:
- Whitelisting permitted users/devices and using a least privilege access control model.
- Sanitising input and parameter hardening.
- Multifactor authentication.
- Obscuring application.
4. Multi-Factor Authentication
Multi-factor authentication is an authentication method where the user has to produce two or more pieces of evidence that they have permission to access a system. For example, when you login to your internet banking system you may have to enter a password and then provide a code which is texted to your registered mobile phone.
We recommend you use at least two factor authentication and strong passwords for all users accessing your critical systems and applications.
5. Administration Privileges
Having administrator privileges can effectively give you the keys to a system, as administrator accounts typically have permission to access and control all data and systems. This makes any account with administrator privileges a prime target for hackers.
Carry out an audit of which users currently have administration privileges – do they really need it? Restrict privileges based on each user’s role and responsibilities. Regularly review the list of users with this level of permission. Ensure that all access to accounts with administration privileges is logged, to allow for any unauthorised access to be tracked and to assist in the incident management process if something untoward does happen. It’s also recommended that rather than being a user’s main account, the administration privileges level account is separate and make sure it has a complex password!
6. Backups
Regular backups of your organization’s critical data, documents and systems are essential. Without them, the impact of a hack or technology failure could be catastrophic. Backups can ensure all of your data is safeguarded and protected. If a data loss does occur a backup can help restore order to your world.
Carry out an audit of all of the applications your organization uses and classify each as high, medium or low priority, based on how important it is to your business. For example, the database containing all of your client information could be high priority, the car park monitoring system could be low priority. Decide how often backups should be created, and how long backups should be stored. Set up systems and processes to ensure this actually happens. However, having an effective backup strategy in place is only the first step. Just as importantly you need to ensure you have a plan for how you restore all of this data when needed.
7. Cyber Awareness
Cyber security isn’t just the IT department’s responsibility. Each and every member of your team has an important role to play in keeping your organization safe. Therefore, having an effective cyber awareness programme and carrying out regular cyber security awareness training is critical to ensuring that your people understand key security risks. It can also help establish a more security-conscious culture across the organization.
Every member of your organization should receive regular training on the security risks you face. CyberCX offer a wide range of options to help educate your employees on cyber awareness.
8. Supplier Security Assessments
A Supplier Security Assessment will allow you to identify if your suppliers have adequate security controls in place to the confidentiality, integrity and availability of your organization’s data and services. It will a uncover any gaps and issues and allow you work with the suppliers to ensure your security concerns are met, and the business relationship continues.
CyberCX can support you with one-off supplier assessments, carry out annual supplier reviews or develop a comprehensive supplier resiliency program for you. We’ll assess the strength of the security controls your suppliers have in place to ensure your organization is adequately protected and prepared.
9. Data Protection
Any information that your business controls or processes needs to be protected. This includes financial information, staff records, and credit card details, even CCTV footage. Any information that can identify an individual, known as personal identifiable information, must be protected. Data Protection Act 2018 and the General Data Protection Regulation (GDPR) now sit alongside each other and work together to ensure the US maintains its very high standard of privacy. Data Protection is not just a legal requirement, it is also crucial to maintaining the reputation and integrity of your organization.
CyberCX can help you protect your data and assist you with meeting regulatory data compliance. Regardless of the where you are with your data protection compliance programme, we can support your business requirements from a fully outsourced Data Protection Officer to support with data mapping, Get in touch to find out more.
10. Cyber Incident Response and Business Continuity
A Cyber Incident Response Plan and Business Continuity Plan will enable your organization to successfully confront and overcome a range of complex, unexpected challenges. An effective plan will help you respond to and reduce the effect of an incident by: limiting damage; improving recovery time; and detailing how communications will be managed within the organization. Planning for a range of challenges can ensure you have the capacity to contend with such challenges efficiently and effectively, reducing the costs to your organization.
At CyberCX we can help you to ensure your organization’s critical operations continue to run during an incident from a full Business Continuity Program aligned to the internationally recognized standard ISO 22301 or one of the services within the program such as our Incident Response Service. Our highly experienced Incident Response Team can be engaged to contain, mitigate and help you recover from the security incident. Get in touch to find out more.
11. ISO 27001
Any information that your business controls or processes needs to be protected. This includes financial information, staff records, and credit card details, even CCTV footage. Any information that can identify an individual, known as personal identifiable information, must be protected. Data Protection Act 2018 and the General Data Protection Regulation (GDPR) now sit alongside each other and work together to ensure the US maintains its very high standard of privacy. Data Protection is not just a legal requirement, it is also crucial to maintaining the reputation and integrity of your organization.
CyberCX can help you protect your data and assist you with meeting regulatory data compliance. Regardless of the where you are with your data protection compliance programme, we can support your business requirements from a fully outsourced Data Protection Officer to support with data mapping, Get in touch to find out more.
Download our full introductory guide which highlights the key areas we believe your organization needs to be aware of, and act on.
How can CyberCX help?
We were founded with the mission of securing our communities and this ethos is at the core of everything we do. We’ve helped thousands of organizations worldwide – from SMEs to large multinationals – understand the potential risks they face. We pride ourselves on delivering the most effective and efficient solution for each client.
To learn more about how CyberCX can help your organization to minimise our cyber risk and prevent costly cyber-attacks speak to one of our consultants today.







